Search for "@FiLiS" returned 623 results

63 min
A look into the Mobile Messaging Black Box
A gentle introduction to mobile messaging and subsequent…

41 min
Extracting keys from FPGAs, OTP Tokens and Door Locks
Side-Channel (and other) Attacks in Practice

58 min
Switches Get Stitches
Industrial System Ownership
58 min
Confessions of a future terrorist
A rough guide to over-regulating free speech with…

56 min
Viva la Vita Vida
Hacking the most secure handheld console

58 min
Baseband Exploitation in 2013
Hexagon challenges

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

61 min
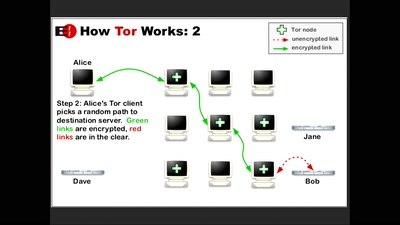
How Alice and Bob meet if they don't like onions
Survey of Network Anonymisation Techniques

55 min
Inside Field Station Berlin Teufelsberg
The story of the NSA listening post – told by an ex-SIGINT…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

63 min
goto fail;
exploring two decades of transport layer insecurity

59 min
De-anonymizing Programmers
Large Scale Authorship Attribution from Executable Binaries…
58 min