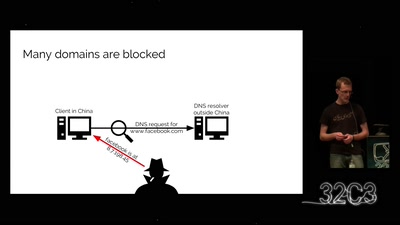
Search for "Misc" returned 575 results

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

62 min
Kyber and Post-Quantum Crypto
How does it work?
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)
59 min
Let's build a quantum computer!
Understanding the architecture of a quantum processor

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

58 min
Protecting Your Privacy at the Border
Traveling with Digital Devices in the Golden Age of…

55 min
The Gospel of IRMA
Attribute Based Credentials in Practice

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

64 min
Magic Lantern
Free Software on Your Camera

53 min
When algorithms fail in our personal lives
Social media break up coordinator

60 min