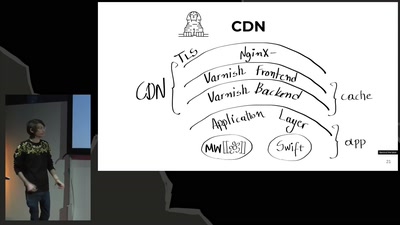
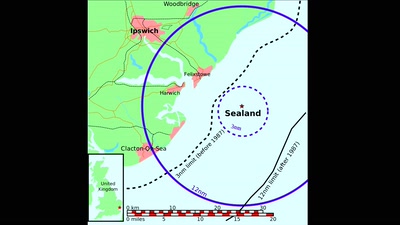
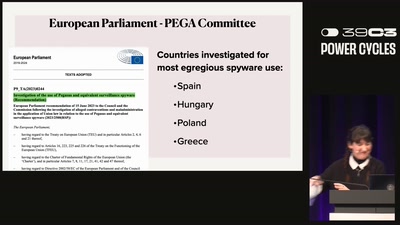
Search for "sECuRE" returned 792 results

31 min
PUFs, protection, privacy, PRNGs
an overview of physically unclonable functions

41 min
Breathing Life into Legacy: An Open-Source Emulator of Legacy Apple Devices
A Dive into Reverse Engineering and Understanding the iPod…

51 min
Digital Identity and Digital Euro
what is the EU up to now?

31 min
TrustZone is not enough
Hijacking debug components for embedded security

29 min
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene
56 min
Iridium Update
more than just pagers

51 min
Funky File Formats
Advanced binary tricks
62 min
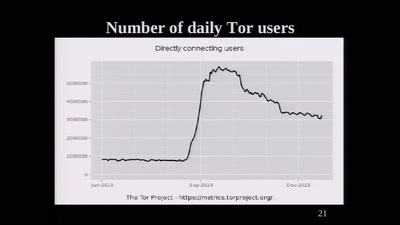
The Tor Network
We're living in interesting times

60 min
Concepts for global TSCM
getting out of surveillance state mode

25 min
»Hard Drive Punch«
Destroying data as a performative act
32 min
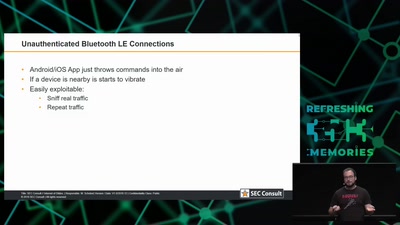
Internet of Dongs
A long way to a vibrant future

38 min
Chaospager
How to construct an Open Pager System for c3

58 min