Search for "Bea" returned 6111 results
61 min
X Security
It's worse than it looks

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

57 min
A Dozen Years of Shellphish
From DEFCON to the DARPA Cyber Grand Challenge

51 min
Wireless Drivers: Freedom considered harmful?
An OpenWrt perspective on the development of Linux 802.11…

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP
59 min
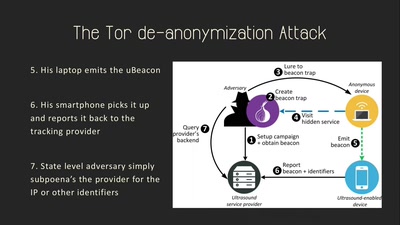
Talking Behind Your Back
On the Privacy & Security of the Ultrasound Tracking…
46 min
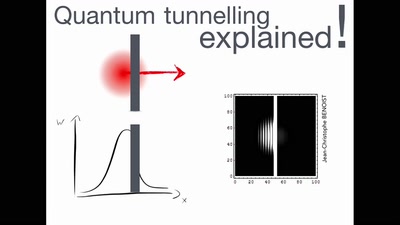
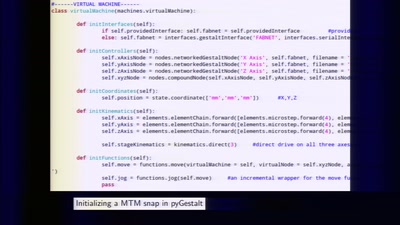
Making machines that make
rapid prototyping of digital fabrication and…

59 min
Hardsploit: A Metasploit-like tool for hardware hacking
A complete toolbox for IoT security
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

61 min
Net Neutrality in Europe
alea iacta est

53 min
When algorithms fail in our personal lives
Social media break up coordinator

31 min
Demystifying Network Cards
Things you always wanted to know about NIC drivers
30 min