Search for "Ralf Lang" returned 614 results

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

58 min
Taming the Chaos: Can we build systems that actually work?
Possible paths from today's ghastly hackery to what…

33 min
Beyond Virtual and Augmented Reality
From Superhuman Sports to Amplifying Human Senses

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy
40 min
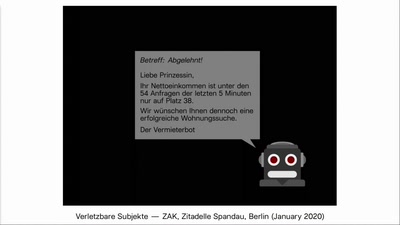
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…
60 min
Wind: Off-Grid Services for Everyday People
Integrating nearby and offline connectivity with the…
45 min
HbbTV Security
OMG - my Smart TV got pr0wn3d

60 min
Glass Hacks
Fun and frightening uses of always-on camera enabled…

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind

51 min