Search for "Bea" returned 6111 results
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect

39 min
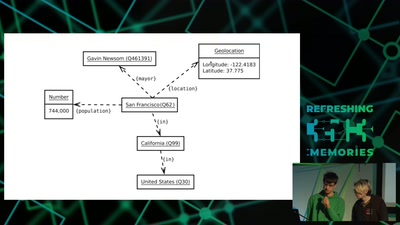
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

63 min
The Global Assassination Grid
The Infrastructure and People behind Drone Killings

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…

30 min
apertus° AXIOM
The first Open Source Cinema Camera

30 min
On Computing Numbers, with an Application to Problems of our Society
Journalism ♥ Computer Science

30 min
Information Control and Strategic Violence
How governments use censorship and surveillance as part of…
58 min
The Ultimate Acorn Archimedes talk
Everything about the Archimedes computer (with zero…

58 min
Baseband Exploitation in 2013
Hexagon challenges
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

59 min
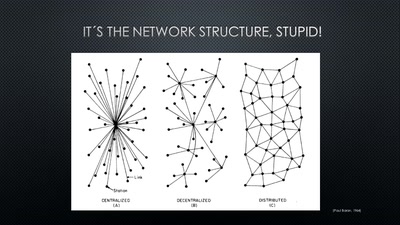
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
60 min
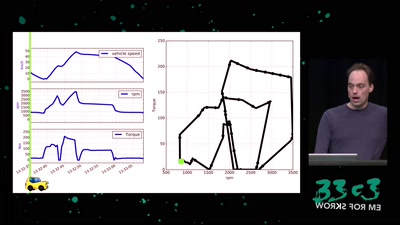
Software Defined Emissions
A hacker’s review of Dieselgate
62 min