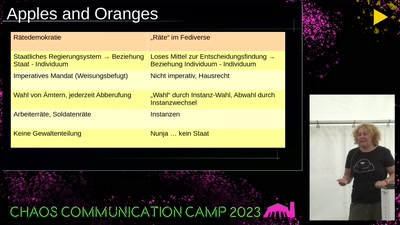
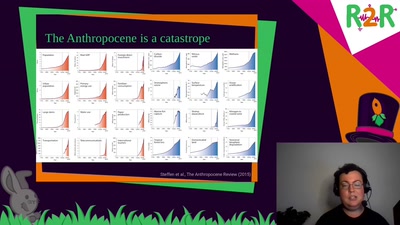
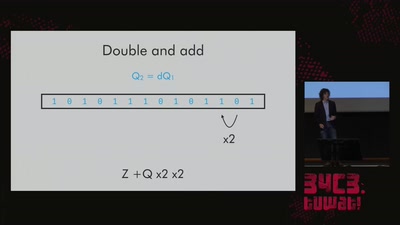
Search for "csk" returned 1256 results

61 min
Computational Meta-Psychology
An Artificial Intelligence exploration into the creation of…

46 min
Practical Mix Network Design
Strong metadata protection for asynchronous messaging

30 min
In Search of Evidence-Based IT-Security
IT security is largely a science-free field. This needs to…
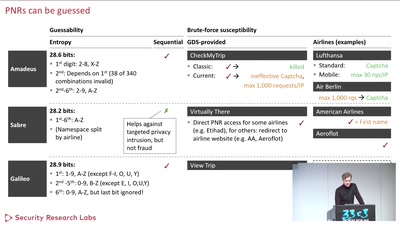
59 min
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
46 min
Maker Spaces in Favelas - Lecture
Engaging social innovation and social innovators
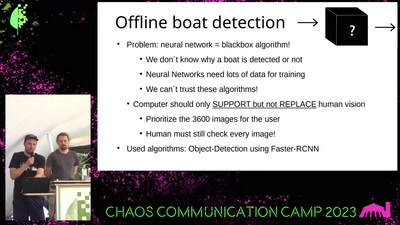
45 min
SearchWing
Open source drones for Search & Rescue
42 min
Union Busting
What is it and why you should care

59 min
Say hi to your new boss: How algorithms might soon control our lives.
Discrimination and ethics in the data-driven society
46 min
The Mission of the MV Louise Michel
"Feminism will be anti-racist or it won´t be"
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

62 min