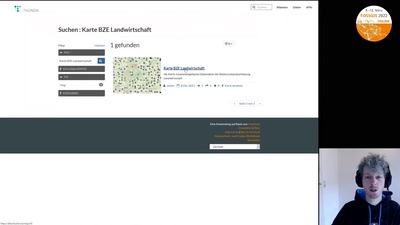
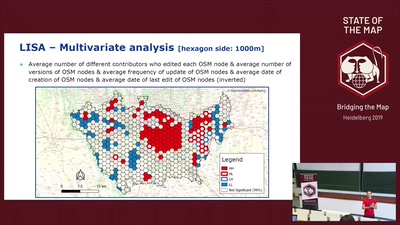
Search for "Isa" returned 9794 results

41 min
Hacking Neural Networks
Eine Einführung in das Hacking von Neuronalen Netzen
28 min
QGIS Web Client 2
Die 2. Generation des Web Clients optimiert für QGIS Server
65 min
Platform-Cooperativism, data ownership and free software
Different paths towards the same goal?

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

39 min
Brennende Wälder und Kommentarspalten
Klimaupdate mit dem FragDenStaat Climate Helpdesk
63 min