Search for "Isa" returned 9806 results

53 min
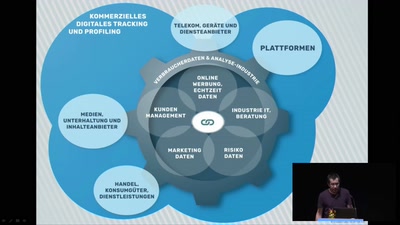
Überwachungskapitalismus
Big Other is watching you.
48 min
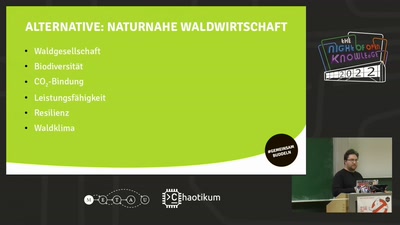
Naturwald Lübeck und #LübeckBuddelt
Bäume pflanzen, auch für Natur und Umwelt ist nicht immer…

41 min
Syslog-ng 4
where log management is heading

34 min