Search for "Isa" returned 9806 results

39 min
Tales of old: untethering iOS 11
Spoiler: Apple is bad at patching

48 min
Linked Open Data
Warum "open" nicht genug ist und wir Daten verlinken müssen.
22 min
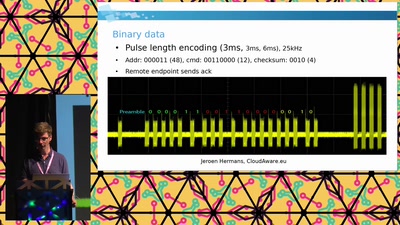
Knock knock, who’s there?
Is your door locked? Are you sure?
8 min
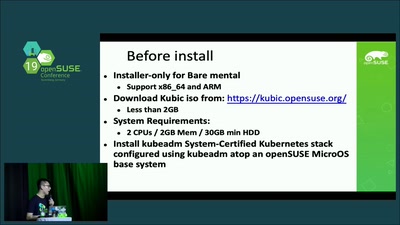
Why you should choose openSUSE Kubic?
openSUSE Kubic is really fun!

56 min
WarGames in memory
what is the winning move?
27 min
Was bringt die Digitalisierung des Energieversorgungssystems?
Ist eine umfassende „Digitalisierung“ die Voraussetzung für…

83 min
Software-Patente. Nicht schon wieder!
Es geht wieder los. Diesmal ist es aber vielleicht das…

59 min
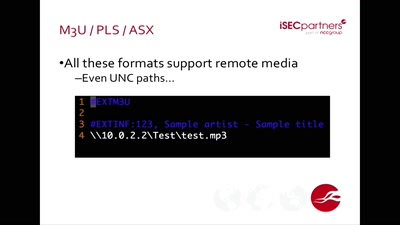
Developments in Coordinated Vulnerability Disclosure
The government is here to help
46 min
Bugged Files
Is Your Document Telling on You?

78 min
Was sind "Open" Source, Data und Standards - und wie funktioniert das?
Die Organisation der Open Geo- und GIS-Welt. Worauf zu…

51 min
Digital Identity and Digital Euro
what is the EU up to now?

28 min
Putting your money on locales
Du hast 5 Geld in der Schweiz – wo ist dein Währungssymbol?

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist
43 min
Chat-Control
now is the time to take action!

59 min
the dark side of the wifi
Warum 802.11ac nicht genug ist und warum es mit 802.11ax…

62 min
Tell no-one
A century of secret deals between the NSA and the telecom…

51 min
Remote Exploits für die Briefwahl in Deutschland
Seit der Abschaffung der Sicherungsmechanismen ist die…

56 min
Console Hacking 2008: Wii Fail
Is implementation the enemy of design?

64 min
Arguments Against Surveillance
'Cos "I Don't Like It" Is Not Enough!
62 min
Cybernetic Cannibalism
Why is Brazil the country of the future?

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

64 min
"Exploit" in theater
post-existentialism is the question, not post-privacy
58 min

