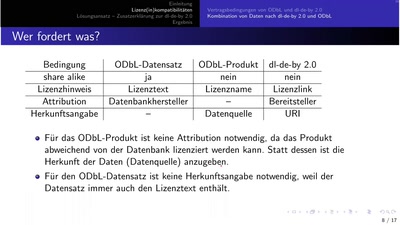
Search for "Isa" returned 9794 results
32 min
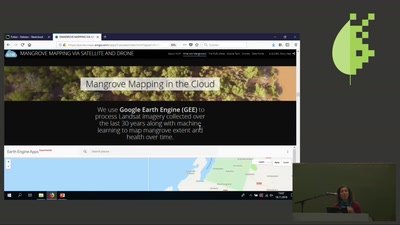
Mangrove Conservation via Satellite
using the latest technology to map and monitor mangroves

62 min
I Control Your Code
Attack Vectors Through the Eyes of Software-based Fault…
28 min
Hardware attacks: hacking chips on the (very) cheap
How to retrieve secret keys without going bankrupt

82 min
Attacking NFC mobile phones
First look at the security of NFC mobile phones

38 min
Quantum Entanglement
An introduction

51 min
Intrusion Detection Systems
Elevated to the Next Level

117 min
CR214 - Hackerethik
Von moralischer Flexibilität und ihren Folgen

63 min
goto fail;
exploring two decades of transport layer insecurity

48 min
Not Soy Fast: Genetically Modified, Resource Greedy, and coming to a Supermarket Near You
The silent march of the multinational GMO soy industry and…

52 min
3G Investigations
Scanning your GPRS/UMTS IP network for fun and profit

40 min
Psychedelic Medicine - Hacking Psychiatry?!
Psychedelic Therapy as a fundamentally new approach to…

46 min