Search for "Isa" returned 9806 results

60 min
"Hallo Welt" in Assembler
Programmieren ist das neue Latein. Wie bringen wir es unter…

9 min
The new mainframe for Edge Computing and Industry 4.0
Is Big Endian continously the right name?

45 min
Homegrown Interactive Tables
Any Technology Sufficiently Advanced is Indistinguishable…
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone
57 min
Taking a Fresh Look at the Fediverse
What Is New For Mastodon And The Wider Ecosystem
31 min
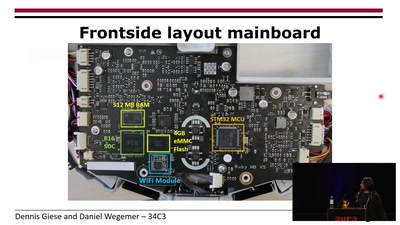
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?
52 min
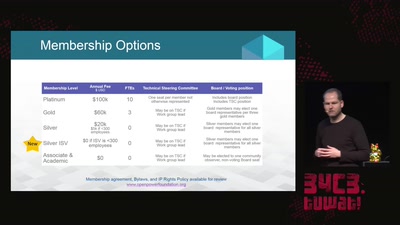
Turris: secure open source router
Who is the root on your router?
31 min
openPower - the current state of commercial openness in CPU development
is there no such thing as open hardware?
43 min
Contain yourselves
The Way We Build Systems is (Still) Wrong
41 min
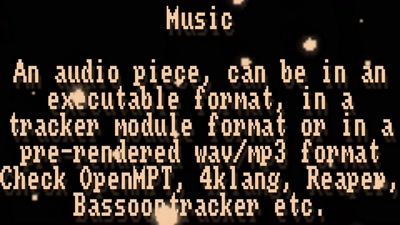
Demoscene now and then
The demoscene is an underground computer art culture.
42 min
Union Busting
What is it and why you should care
60 min
Data Retention in the EU five years after the Directive
Why the time is now to get active
53 min
CCC Office, die neue Software
Was ist der Stand, was kann die neue Software und was wird…

34 min
Social Cooling - big data’s unintended side effect
How the reputation economy is creating data-driven…

57 min
Secure Code
Why developing Secure Software is like playing Marble…

36 min
PolyCoin - A game played across MCH
How it works and what is inside it
36 min
Live: Firebird: the high performance database that you didnt know was already on your…
Installed with Libre Office, Firebird is a vastly capable…
47 min
Test-Driven Web Development
Treating your web application like the grown-up it is
17 min
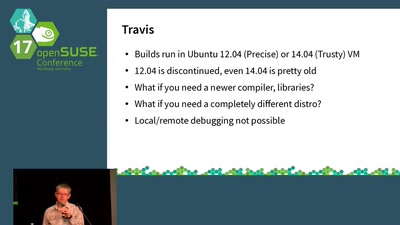
Continuous Integration using Travis and Docker
There is no excuse for NOT using continuous integration

44 min
Why technology sucks
If technology is the solution, politicians are the problem
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle

32 min
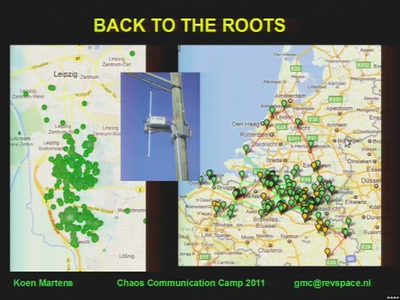
Craft, leisure, and end-user innovation
How hacking is conceived in social science research
40 min
A modern manifest of cyberspace
The internet is dead, long live the internet

39 min
