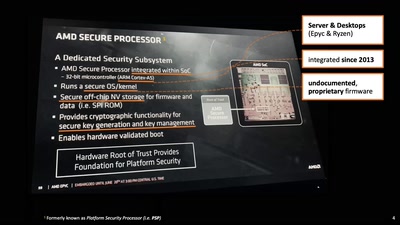
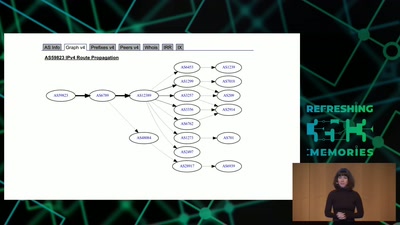
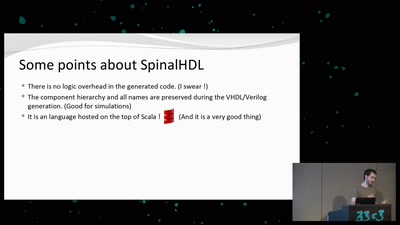
Search for "W. Heck" returned 1246 results

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine

60 min
Shopshifting
The potential for payment system abuse

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

57 min
Du kannst alles hacken – du darfst dich nur nicht erwischen lassen.
OpSec für Datenreisende

22 min
Trust us and our business will expand!
Net-activism strategies against fake web companies

63 min
goto fail;
exploring two decades of transport layer insecurity
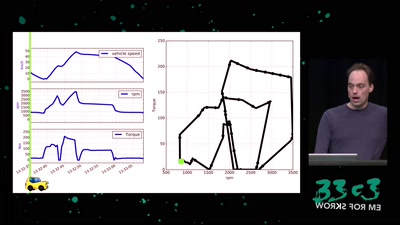
60 min
Software Defined Emissions
A hacker’s review of Dieselgate
27 min
Maritime Robotics
Hackers, I call thee to our Oceans!
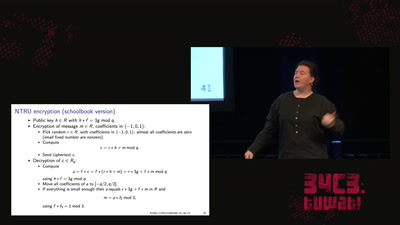
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…

47 min