Search for "nika" returned 122 results
41 min
Demoscene now and then
The demoscene is an underground computer art culture.

42 min
Jugend Hackt
Chaos Family

62 min
Kyber and Post-Quantum Crypto
How does it work?

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…

37 min
Hacking (with) a TPM
Don't ask what you can do for TPMs, Ask what TPMs can do…

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks

58 min
PLC-Blaster
Ein Computerwurm für PLCs

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database
40 min
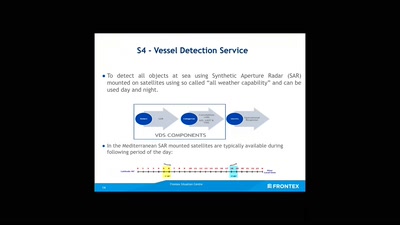
No roborders, no nation, or: smile for a European surveillance propagation
How an agency implements Fortress Europe by degrading…

29 min