Search for "sudden6" returned 98 results
62 min
A New Kid on the Block
Conditions for a Successful Market Entry of Decentralized…

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

61 min
Correcting copywrongs
European copyright reform is finally on the horizon

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

32 min
The Case for Scale in Cyber Security
Security Track Keynote
54 min
How medicine discovered sex
Introduction to sex- and gender-sensitive medicine

52 min
The Internet of rubbish things and bodies
A review of the best art & tech projects from 2019. With a…
28 min
SatNOGS: Crowd-sourced satellite operations
Satellite Open Ground Station Network

30 min
libusb: Maintainer fail
How I failed to run an open source project

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…

54 min
How (not) to build autonomous robots
Fables from building a startup in Silicon Valley
31 min
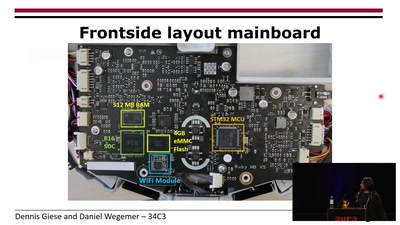
Unleash your smart-home devices: Vacuum Cleaning Robot Hacking
Why is my vacuum as powerful as my smartphone?
53 min
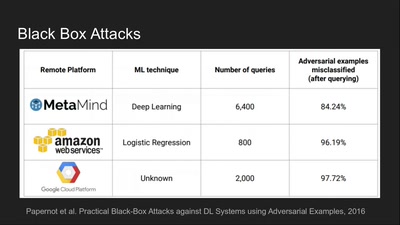
Deep Learning Blindspots
Tools for Fooling the "Black Box"

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
44 min
Replication Prohibited
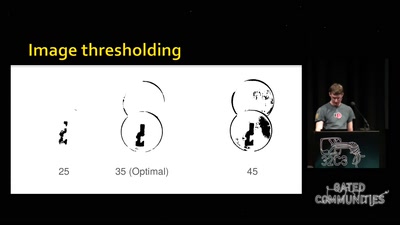
3D printed key attacks

60 min
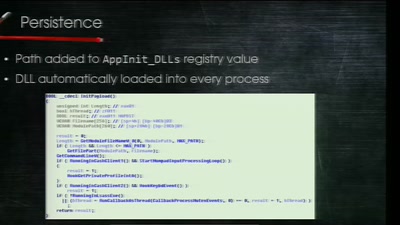
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI
58 min
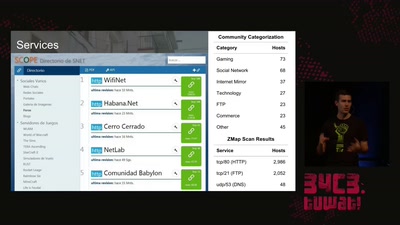
The Internet in Cuba: A Story of Community Resilience
Get a unique tour of some of the world’s most unusual…
56 min