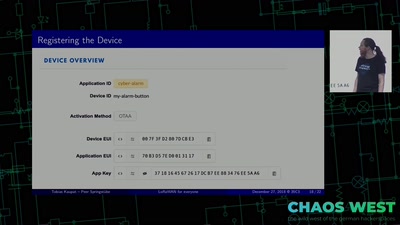
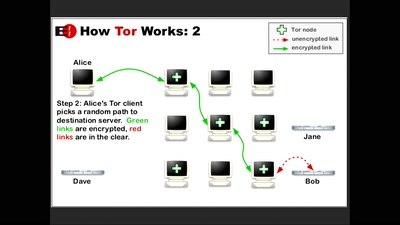
Search for "Udo Vetter" returned 1176 results
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
31 min
DPRK Consumer Technology
Facts to fight lore

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study

46 min
The nextpnr FOSS FPGA place-and-route tool
the next step forward in open source FPGA tools
60 min
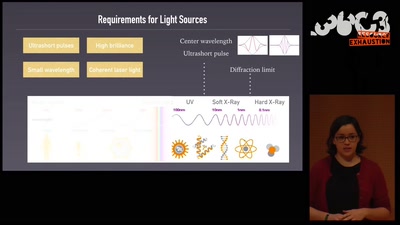
An ultrashort history of ultrafast imaging
Featuring the shortest movies and the largest lasers
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
58 min
Hacking how we see
A way to fix lazy eye?
25 min
Keys of Fury
Type In Beyond the Scrolling Horizon

56 min
Viva la Vita Vida
Hacking the most secure handheld console

60 min
Lets break modern binary code obfuscation
A semantics based approach
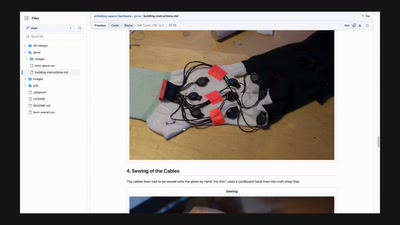
39 min
The Unfolding Space Glove
A Wearable for the Visually Impaired Translating 3D Vision…
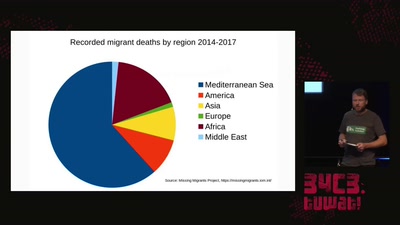
32 min
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized

31 min
Demystifying Network Cards
Things you always wanted to know about NIC drivers

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…
66 min