Search for "Ralf" returned 779 results

61 min
Untrusting the CPU
A proposal for secure computing in an age where we cannot…

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

60 min
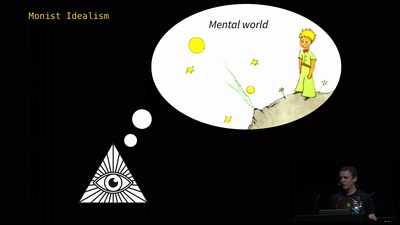
From Computation to Consciousness
How computation helps to explain mind, universe and…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…
62 min
The Ghost in the Machine
An Artificial Intelligence Perspective on the Soul

60 min
Mein Bot, der Kombattant
Operative Kommunikation im digitalen Informationskrieg

64 min
Source Code and Cross-Domain Authorship Attribution
The Role of Stylometry in Privacy
62 min
Machine Dreams
Dreaming Machines

61 min
The architecture of a street level panopticon
How drones, IMSI Catchers, and cameras are shaping our…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…
59 min