Search for "Ben" returned 8957 results

54 min
Hacking Cisco Phones
Just because you are paranoid doesn't mean your phone isn't…

30 min
Open source photovoltaics
power for off-grid devices
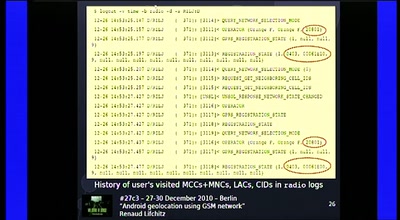
63 min
Android geolocation using GSM network
"Where was Waldroid?"

65 min
Practical RFID Attacks
writing, sniffing & emulating 13.56MHz RFID tags with…

45 min
Router and Infrastructure Hacking
"First we take Manhattan, then we take Berlin..."

59 min
Logical Language Lojban
A Hackers' /Spoken/ Language?!

45 min
Finding and Preventing Buffer Overflows
An overview of static and dynamic approaches

21 min
Closing Event
Good Bye and have a safe trip home!

57 min
802.11 Packets in Packets
A Standard-Compliant Exploit of Layer 1

61 min
PyPy - the new Python implementation on the block
Language/VM R&D, whole program type inference, translation…

63 min
Print Me If You Dare
Firmware Modification Attacks and the Rise of Printer…

58 min