Search for "Isa" returned 9795 results

31 min
The DRM Of Pacman
Copy protection schemes of way back then and how they…

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…

69 min
Mobile phone call encryption
Encrypting (GSM) mobile phone calls over VPN with an…

46 min
You can -j REJECT but you can not hide: Global scanning of the IPv6 Internet
Finding interesting targets in 128bit of entropy

59 min
State of Emergent Democracy
Where are we today?

40 min
An introduction to Firmware Analysis
Techniques - Tools - Tricks
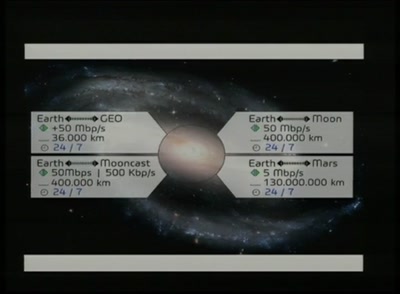
128 min
A part time scientists' perspective of getting to the moon
presenting the first German Team participating in the…

38 min
The impact of quantum computers in cybersecurity
Estimating the costs of algorithms for attacks and defense…

52 min
DevOps, delivering value in a judgmental world
Golden Hammers never had it so good
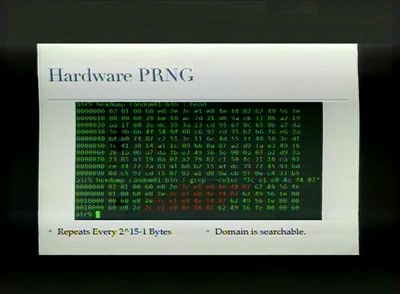
55 min
Building a Debugger
Open JTAG with Voltage Glitching

68 min
"Spoilers, Reverse Green, DECEL!" or "What's it doing now?"
Thoughts on the Automation and its Human interfaces on…

62 min
Calafou, postcapitalist ecoindustrial community
Building a space for grassroots sustainable technology…
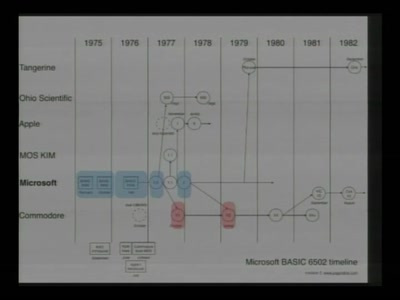
61 min
The Ultimate Commodore 64 Talk
Everything about the C64 in 64 Minutes

60 min
Crypto Wars Part II
The Empires Strike Back

54 min
![[SPONSOR] BearingPoint Vortrag: Künstliche Intelligenz - Anwendungen und Trends](https://static.media.ccc.de/media/events/glt/2022/306-2d2d9bdd-ee4b-5183-a34c-4d8f1c012139.jpg)