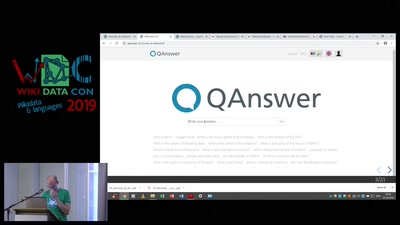
Search for "Finn" returned 2072 results

52 min
The Internet of rubbish things and bodies
A review of the best art & tech projects from 2019. With a…
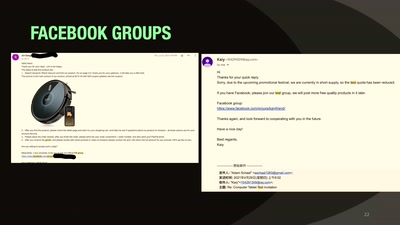
41 min
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.
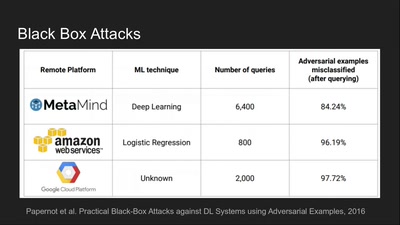
53 min
Deep Learning Blindspots
Tools for Fooling the "Black Box"

58 min
Überwachen und Sprache
How to do things with words

53 min
Console Hacking 2016
PS4: PC Master Race

71 min
10.000 Seiten später
Welche Spuren der Klimabericht bei mir hinterlassen hat

16 min
Youth Hacking 4 Freedom
Hacking competition for teenagers from Europe

42 min
Ist die Demokratie noch zu retten?
Politikwissenschaftliche Demokratieforschung in der Krise
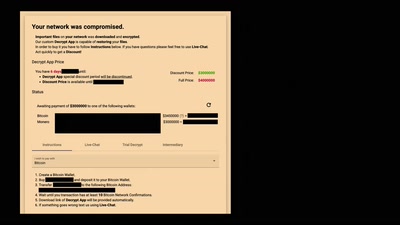
61 min
Hirne hacken: Hackback Edition
Wir verhandeln mit Erpressern, damit Ihr es nicht müsst.

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…
16 min
Decent Patterns
an Open UX Library for Decentralisation

64 min