Search for "glow" returned 1361 results
35 min
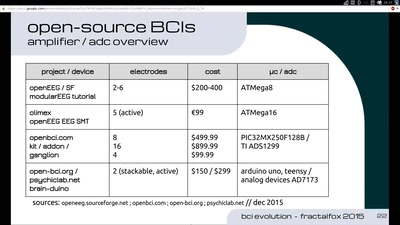
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress

61 min
An Elevator to the Moon (and back)
Space Transportation and the Extraterrestrial Imperative

62 min
Kyber and Post-Quantum Crypto
How does it work?

60 min
My Robot Will Crush You With Its Soft Delicate Hands!
How to design and fabricate soft robots using everyday…

51 min
The GNU Name System
A Decentralized PKI For Social Movements

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…
43 min
No PoC? No Fix! - A sad Story about Bluetooth Security
It is just a broken memcpy in the Bluetooth stack. Do we…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

59 min
TamaGo - bare metal Go framework for ARM SoCs.
Reducing the attack surface with pure embedded Go.

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

33 min
UPSat - the first open source satellite
Going to space the libre way
41 min
SCADA StrangeLove 2
We already know

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

60 min