Search for "Germany) " returned 991 results

59 min
We should share our secrets
Shamir secret sharing: How it works and how to implement it
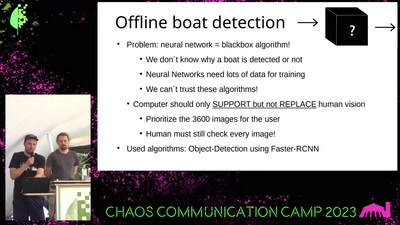
45 min
SearchWing
Open source drones for Search & Rescue

54 min
Attacking Chrome IPC
Reliably finding bugs to escape the Chrome sandbox

32 min
History and implications of DRM
From tractors to Web standards

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches

50 min
Heimlich-Manöver
Best of Informationsfreiheit & Gefangenenbefreiung
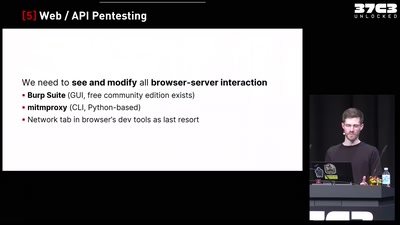
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide

63 min
All cops are broadcasting
TETRA unlocked after decades in the shadows
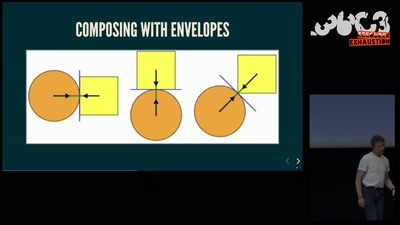
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!

49 min
Toward a Cognitive "Quantified Self"
Activity Recognition for the Mind
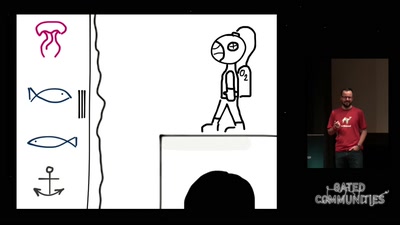
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…
58 min
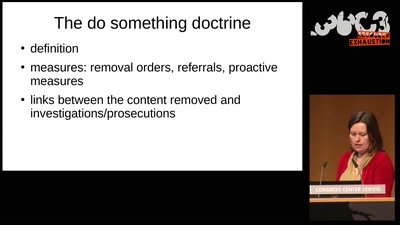
Confessions of a future terrorist
A rough guide to over-regulating free speech with…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
36 min
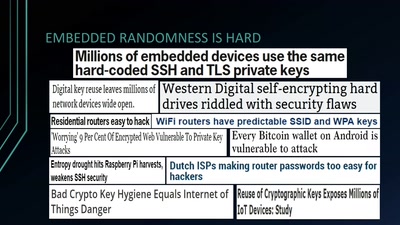
Wheel of Fortune
Analyzing Embedded OS Random Number Generators

40 min
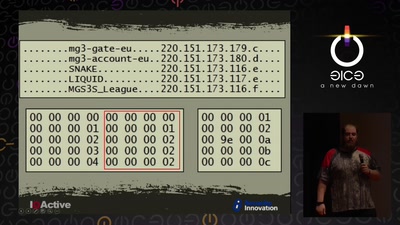
Intercoms Hacking
Call the frontdoor to install your backdoors
55 min
Cyber Necromancy
Reverse Engineering Dead Protocols
59 min







