Search for "Joi Ito" returned 1334 results
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish

36 min
Von Zebrastreifen, offenen Daten und verschlossenen Verwaltungen
Luxemburgs kreative Route zur Amtstransparenz
31 min
The Economic Consequences of Internet Censorship
Why Censorship is a Bad Idea for Everyone

30 min
Science is broken
How much can we trust science in light failed replications,…
64 min
On the Security and Privacy of Modern Single Sign-On in the Web
(Not Only) Attacks on OAuth and OpenID Connect
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…
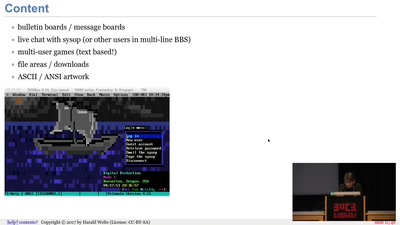
61 min
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN
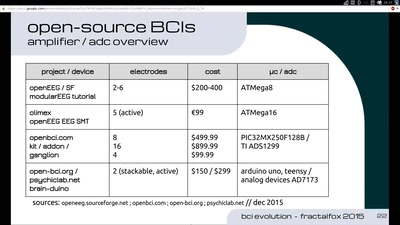
35 min
Evolution of Brain-Computer Interfaces
The future of Neuro-Headsets and concepts towards…
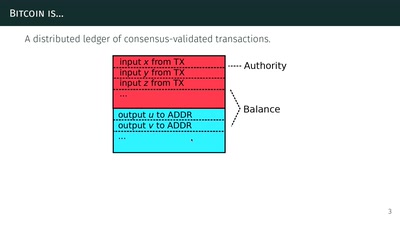
31 min
The Zcash anonymous cryptocurrency
or zero-knowledge succinct non-interactive arguments of…
72 min