Search for "M" returned 11770 results

25 min
Network Traffic Analysis using Deep Packet Inspection and Data Visualization
Eventpad: the Sublime editor for network traffic
59 min
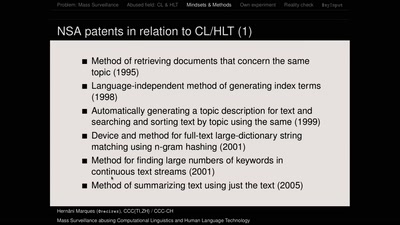
Mass Surveillance abusing Computational Linguistics and Human Language Technology
Mind-sets, state-of-the-art methods and practices according…
36 min
Smart Home Security with Tor
Using TOR for securing Smart Homes from prying eyes

33 min
Social cooling
How the reputation economy is turning us into conformists

52 min
An academic's view to incident response
It's all fun and games until reality starts kicking you in…

50 min
Art Tech Activism Privacy and Cool Robots
Not only hackers do Security, Privacy and Hacking. Want to…

27 min
Detecting a breach from an attackers perspective.
We're gonna regret this
40 min
Improving security with Fuzzing and Sanitizers
Free and open source software has far too many security…

52 min
Privacy Design Strategies
Doing well is good enough

43 min
Hack North Korea
Flash Drives for Freedom
42 min
Beyond the Titanic
Learning from dataleaks
58 min
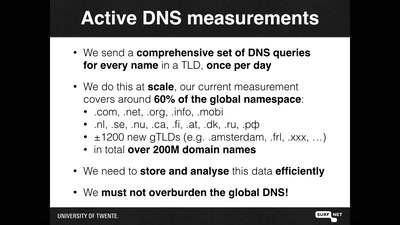
OpenINTEL: digging in the DNS with an industrial size digger
I measured 60% of the DNS, and I found this
61 min
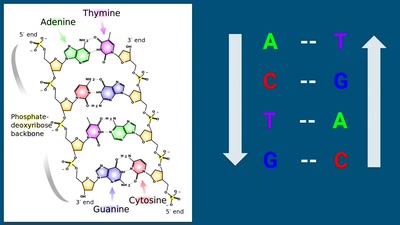
DNA: The Code of Life
Surprise: it is fully digital!
64 min
Are Whistleblowers safer today than they were at OHM2013?
Current case studies of whistleblowing in Europe, and how…
156 min
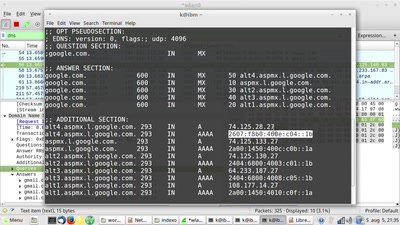
Network concepts introduction & wireshark workshop
The legendary workshop that teaches you how network really…
38 min
Hacking on a boat
Fun with onboard maritime systems

37 min