Search for "John" returned 1055 results

64 min
Technical aspects of the surveillance in and around the Ecuadorian embassy in London
Details about the man hunt for Julian Assange and Wikileaks

59 min
Financial surveillance
Exposing the global banking watchlist
61 min
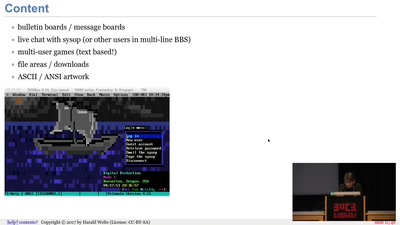
BBSs and early Internet access in the 1990ies
Modems, FIDO, Z-Netz, Usenet, UUCP, SLIP and ISDN

61 min
Net Neutrality in Europe
alea iacta est

61 min
Vacuum robot security and privacy
prevent your robot from sucking your data

32 min
Verified Firewall Ruleset Verification
Math, Functional Programming, Theorem Proving, and an…

61 min
Uncaging Microchips
Techniques for Chip Preparation

63 min
Reproducible Builds
Moving Beyond Single Points of Failure for Software…
65 min
Rocket science – how hard can it be?
First steps into space with sounding rockets

55 min
Vehicle immobilization revisited
Uncovering and assessing a second authentication mechanism…

60 min
On the insecure nature of turbine control systems in power generation
A security study of turbine control systems in power…

41 min
NGI Zero: A treasure trove of IT innovation
Resilient. Trustworthy. Sustainably Open.

53 min
Surveilling the surveillers
About military RF communication surveillance and other…

60 min
Building a high throughput low-latency PCIe based SDR
Lessons learnt implementing PCIe on FPGA for XTRX Software…

60 min
Attacking end-to-end email encryption
Efail, other attacks and lessons learned.

63 min
Reconstructing narratives
transparency in the service of justice

32 min