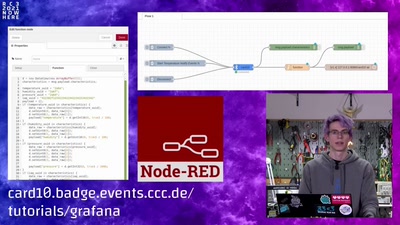
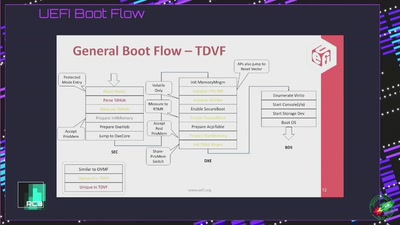
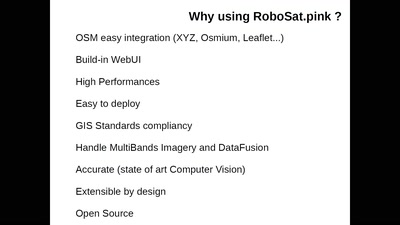
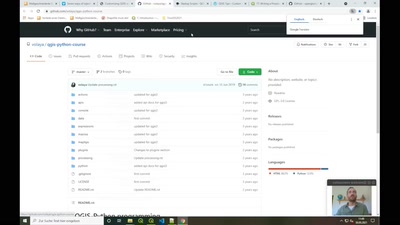
Search for "Isa" returned 9796 results

30 min
Rethinking openSUSE release tooling and the build service
Simplify, improve, and increase transparency
42 min
First Privacy, Now Safety:
An Anthology of Tales from the Front Lines of Cyber…

29 min
The Urban Organism
Hacking [in] Hong Kong

60 min
Buffering sucks!
An attempt of calculating the economic cost of buffering.

42 min
Jugend Hackt
Chaos Family

50 min
Using Qt Creator For Desktop And Embedded Development
Creating Nice Interfaces With C++ And Declarative UI
19 min
c3 MorningShow
Tag 1

11 min
c3 NewsShow
Tag 2
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…
56 min
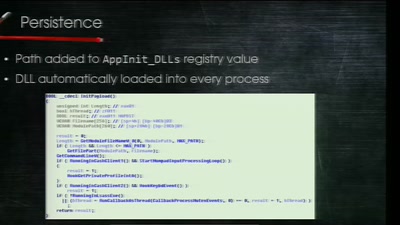
Electronic Bank Robberies
Stealing Money from ATMs with Malware
57 min
Eating in the Anthropocene
Transgenic Fish, Mutagenic Grapefruits and Space Potatoes

39 min
ID Cards in China: Your Worst Nightmare
In China Your ID Card Knows Everything

32 min