Search for "Ben" returned 8958 results

43 min
Twisting timing in your favour
Finding and exploiting concurrency issues in software

56 min
"The Concert"
a disconcerting moment for free culture
54 min
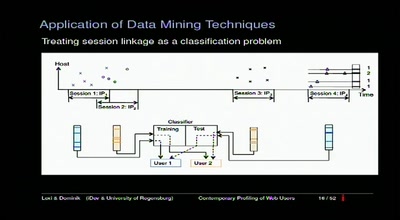
Contemporary Profiling of Web Users
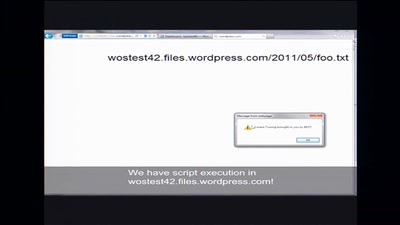
On Using Anonymizers and Still Get Fucked

71 min
Estonia and information warfare
What really happened in Estonia, and what does it mean to…
33 min
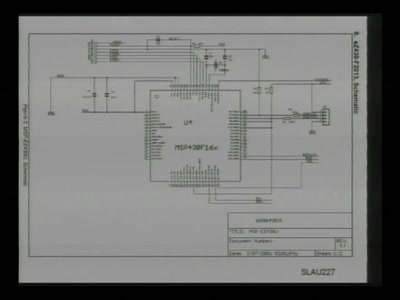
Repurposing the TI EZ430U
with msp430static, solder, and syringe

37 min
Hacking Space
Cheap access to Space using lighter then air methods
46 min
Tits & Bits
pr0n 2.0

57 min
Page Fault Liberation Army or Gained in Translation
a history of creative x86 virtual memory uses

47 min
Peer-to-peer under the hood
An in-depth look at p2p algorithmics

49 min
Access to Knowledge
Copyright, Patents and Politics at the World Intellectual…

47 min
Hacking the Bionic Man
Science fiction or security in 2040?

59 min
An Overview of Secure Name Resolution
DNSSEC, DNSCurve and Namecoin
28 min
Ooops I hacked my PBX
Why auditing proprietary protocols matters

48 min
Moonbounce Radio Communication
To the Moon and back in two seconds. The joy of light speed…
48 min
One Token to Rule Them All
Post-Exploitation Fun in Windows Environments

53 min
Automated Botnet Detection and Mitigation
How to find, invade and kill botnets automated and…
62 min
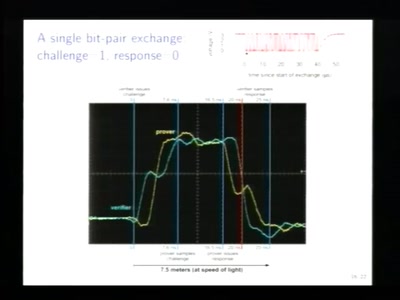
Relay attacks on card payment: vulnerabilities and defences
Keeping your enemies close

49 min