Search for "Jan" returned 8886 results
37 min
Hausvernetzung
Mehr als 1 Wohnung mit mehr als 1 LAN/WLAN

53 min
Towards a Single Secure European Cyberspace?
What the European Union wants. What the hackerdom can do..
47 min
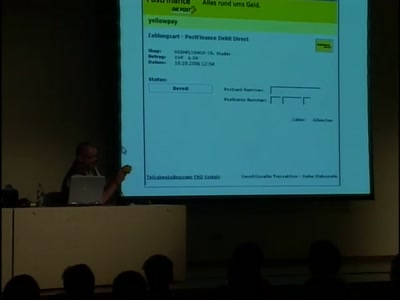
A not so smart card
How bad security decisions can ruin a debit card design

39 min
Recharge your batteries with us
– an empowering journey through the energy transition
67 min
Life is a Holodeck!
An overview of holographic techniques
25 min
The Mainframe
An alternative platform for openSUSE

63 min
Virtuelle Sicherheit
Mandatory Access Control und TPM in Xen

62 min
Vehicular Communication and VANETs
The future and security of communicating vehicles

45 min
Introduction to matrix programming: trance codes
How to recognize trance coded communication patterns

45 min
Router and Infrastructure Hacking
"First we take Manhattan, then we take Berlin..."

53 min
Nerds und Geeks zwischen Stereotyp und Subkultur
Eine kulturanthropologische Untersuchung

59 min
CCC Jahresrückblick
Ein Überblick über die Aktivitäten des Clubs 2006

71 min
Sie haben das Recht zu schweigen
Durchsuchung, Beschlagnahme, Vernehmung - Strategien für…

51 min
Schlossöffnung bei der Staatssicherheit der DDR
Werkzeuge und Vorgehen der STASI

63 min
Biometrics in Science Fiction
2nd Iteration

47 min
Chaos und Kritische Theorie
Adorno, Wilson und Diskordianismus

61 min
Fnord Jahresrückblick
Wir helfen Euch, die Fnords zu sehen
51 min