Search for "Lea Rain" returned 1140 results

60 min
Why is GPG "damn near unusable"?
An overview of usable security research

22 min
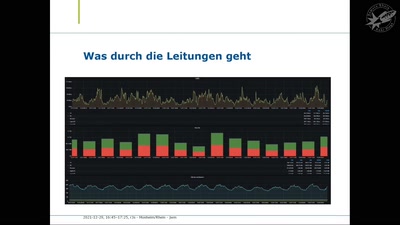
Trust us and our business will expand!
Net-activism strategies against fake web companies

115 min
Methodisch inkorrekt!
Die Wissenschaftsgala vom 34C3
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

29 min
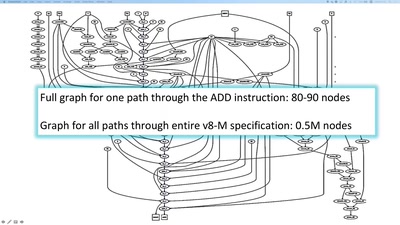
Infocalypse now: P0wning stuff is not enough
Several failure modes of the hacker scene

33 min
Interplanetary Colonization
the state at the beginning of the 21st Century
59 min
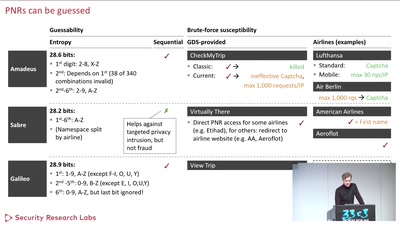
Where in the World Is Carmen Sandiego?
Becoming a secret travel agent
40 min
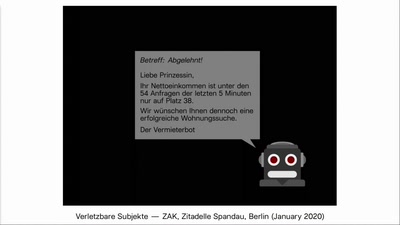
Wohnungsbot: An Automation-Drama in Three Acts
A media-art project which automates the search for flats in…
57 min
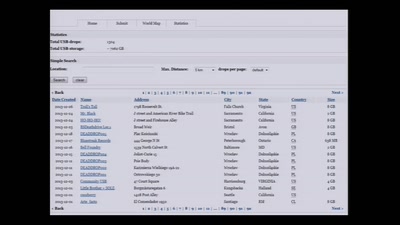
Hello World!
How to make art after Snowden?
42 min
Hacking the Nintendo Game & Watch
Your princess is AES encrypted in another castle

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…

52 min