Search for "Matt Hardy" returned 244 results
61 min
Grow your own planet
How simulations help us understand the Universe
52 min
DNGerousLINK
A Deep Dive into WhatsApp 0-Click Exploits on iOS and…
47 min
Hillbilly Tracking of Low Earth Orbit
Repurposing an Inmarsat Dish
62 min
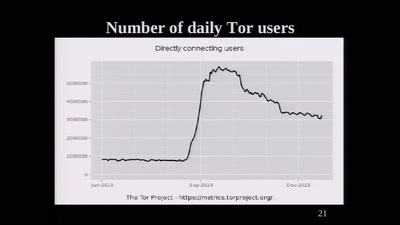
The Tor Network
We're living in interesting times
113 min
Das Bits&Bäume-Sporangium
8 Mikrokosmen, 8 Expert*innen, je 8 Minuten zu…

58 min
How risky is the software you use?
CITL: Quantitative, Comparable Software Risk Reporting
55 min
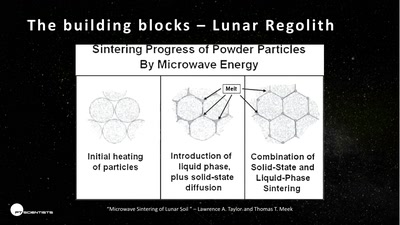
3D printing on the moon
The future of space exploration

60 min
osmo-gmr: What's up with sat-phones ?
Piecing together the missing bits
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
47 min
Finding Vulnerabilities in Internet-Connected Devices
A Beginner’s Guide
43 min
If It Ain't Broken, Do Fix It
Building Modern Cryptography

25 min
Regulating Autonomous Weapons
The time travelling android isn’t even our biggest problem
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…
29 min
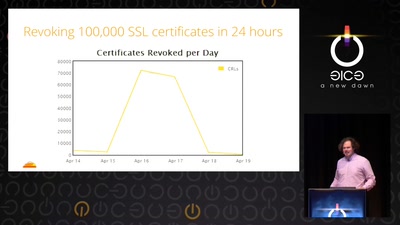
Heartache and Heartbleed: The insider’s perspective on the aftermath of Heartbleed
The untold story of what really happened, how it was…
55 min
SigOver + alpha
Signal overshadowing attack on LTE and its applications

57 min
How I Learned to Stop Reinventing and Love the Wheels
or having FUN with (home/hackerspace) robotics

55 min
3D Casting Aluminum
Too Much Fun with Microwaves

63 min