Search for "Olga" returned 123 results

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

62 min
Kyber and Post-Quantum Crypto
How does it work?

36 min
A Blockchain Picture Book
Blockchain origins and related buzzwords, described in…

32 min
The Case for Scale in Cyber Security
Security Track Keynote

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

29 min
Pegasus internals
Technical Teardown of the Pegasus malware and Trident…
32 min
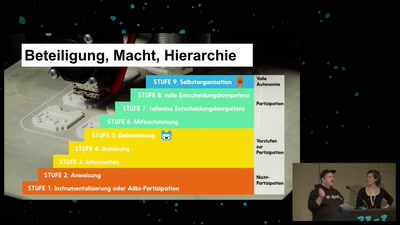
Von Alpakas, Hasenbären und Einhörnern – Über Anerkennungskultur
Wie Wertschätzung in (Tech-)Communities gelingen kann

44 min
What the cyberoptimists got wrong - and what to do about it
Tech unexeptionalism and the monopolization of every…

32 min
Finding the Weak Crypto Needle in a Byte Haystack
Automatic detection of key-reuse vulnerabilities

48 min
Seidenstraße
The Making of…
31 min
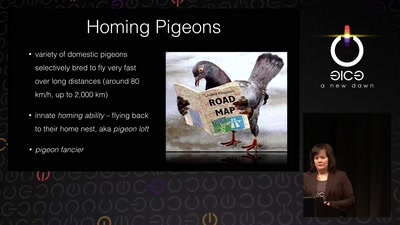
Living Drones
From war pigeons in 1914 to cyborg moths in 2014
54 min