Search for "Sven Brauch" returned 181 results

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

58 min
Glitching For n00bs
A Journey to Coax Out Chips' Inner Secrets

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

56 min
Viva la Vita Vida
Hacking the most secure handheld console
59 min
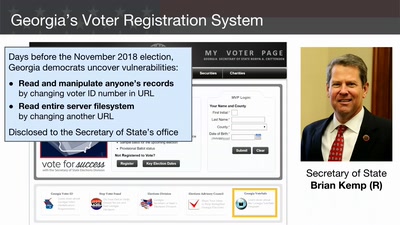
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

120 min
Hacken, dass...?
Ack, die Wette gilt!

31 min
The Clash of Digitalizations
The Devolution of Arab Men from Humans to Digital Fodder
39 min
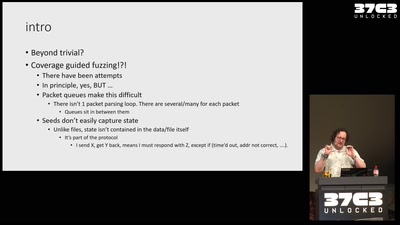
Fuzzing the TCP/IP stack
beyond the trivial

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

61 min
Deploying TLS 1.3: the great, the good and the bad
Improving the encrypted the web, one round-trip at a time
![A NEW HOPE [de]](https://static.media.ccc.de/media/congress/2023/11904-ebbb938f-c1f7-4aad-a37d-ba1aea84eac0.jpg)
40 min
A NEW HOPE [de]
Ein Pep Talk für alle, die gerade verzweifeln

58 min
When hardware must „just work“
An inside look at x86 CPU design

60 min
On Digitalisation, Sustainability & Climate Justice
A critical talk about sustainability, technology, society,…
21 min
Designing PCBs with code
Is designing circuits with code instead of CAD the future…

55 min
ZombieLoad Attack
Leaking Your Recent Memory Operations on Intel CPUs

126 min
Logbuch:Netzpolitik 466
Die Ibiza-Affäre und ihre Folgen

60 min
The Fight for Encryption in 2016
Crypto fight in the Wake of Apple v. FBI

39 min
DISNOVATION.ORG
Disobedient Innovation
37 min
Inside the AMD Microcode ROM
(Ab)Using AMD Microcode for fun and security

61 min
Trustworthy secure modular operating system engineering
fun(ctional) operating system and security protocol…

53 min