Search for "ceres-c" returned 206 results

60 min
Free Software and Hardware bring National Sovereignty
Gaza as a case study
35 min
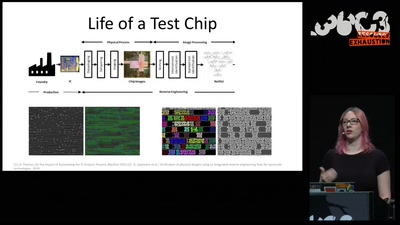
Understanding millions of gates
Introduction to IC reverse engineering for…

95 min
Platform System Interface
Design und Evaluation holistischer Computerarchitektur

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation
59 min
NSA Points of Presence in AT
Vortrag mit aktuellen Fotos aus luftigen Perspektiven
50 min
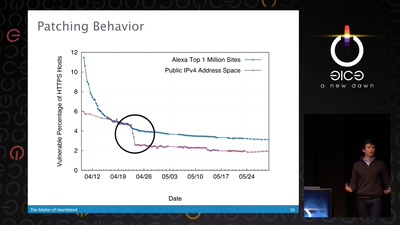
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

60 min
A Story of Discrimination and Unfairness
Prejudice in Word Embeddings
38 min
ARMore: Pushing Love Back Into Binaries
Aarch64 binary rewriting adventures but mostly pains

34 min
Scuttlebutt
The decentralized P2P gossip protocol

31 min
TrustZone is not enough
Hijacking debug components for embedded security

58 min
Switches Get Stitches
Industrial System Ownership

49 min
Dissecting VoLTE
Exploiting Free Data Channels and Security Problems
36 min
Unlocking the Road Ahead: Automotive Digital Forensics
A deep dive into an underrepresented research area
60 min
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
38 min