Search for "vater" returned 1262 results
62 min
Getting software right with properties, generated tests, and proofs
Evolve your hack into robust software!
57 min
A New Dark Age
Turbulence, Big Data, AI, Fake News, and Peak Knowledge

55 min
What is Good Technology?
Answers & practical guidelines for engineers.

30 min
The Machine To Be Another
Exploring identity and empathy through neuroscience,…
38 min
A deep dive into the world of DOS viruses
Explaining in detail just how those little COM files…
47 min
Jailbreaking iOS
From past to present

60 min
Shopshifting
The potential for payment system abuse

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
63 min
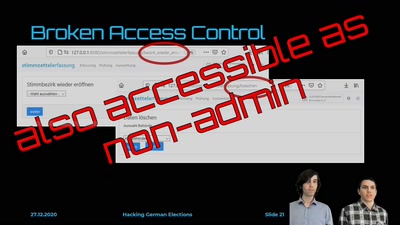
Hacking German Elections
Insecure Electronic Vote Counting - How It Returned and Why…
26 min
Der 33 Jahrerückblick
Technology and Politics in Congress Talks, from 1984 to now
26 min
Eine kleine Geschichte der Parlamentsschlägerei
Schlagende Argumente, fliegende Fäuste
65 min
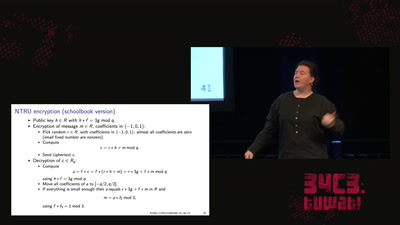
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

35 min