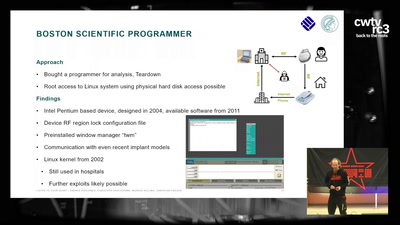
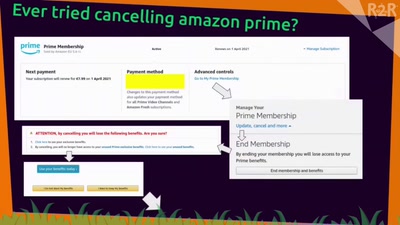
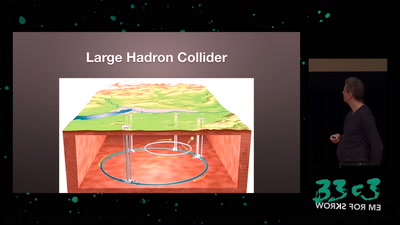
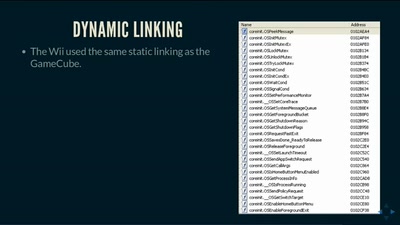
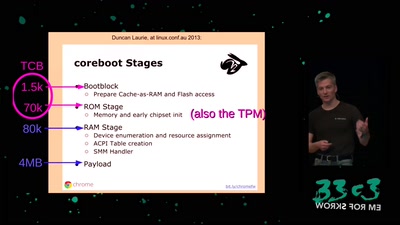
Search for "Mike Place" returned 1157 results
42 min
Wifibroadcast
How to convert standard wifi dongles into digital broadcast…
60 min
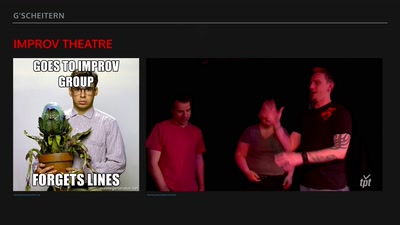
G’scheitern
The art of failure taught by improv theatre
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy

30 min
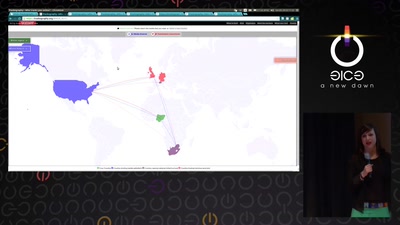
Privacy and Consumer Markets
Reversing the Surveillance Business Model
31 min
Trackography
You never read alone

60 min
Everything you always wanted to know about Certificate Transparency
(but were afraid to ask)

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

45 min
To Protect And Infect
The militarization of the Internet

59 min
Pointing Fingers at 'The Media'
The Bundestagswahl 2017 and Rise of the AfD
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

22 min