Search for "Udo Vetter" returned 1176 results
60 min
The Perl Jam 2
The Camel Strikes Back

31 min
Mr Beam goes Kickstarter
Lessons learned from crowdfunding a hardware project
83 min
Der Weisheit
Eine Stunde Lebenskunde - 10. Staffelfinale
65 min
LatticeHacks
Fun with lattices in cryptography and cryptanalysis

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…

60 min
Are machines feminine?
exploring the relations between design and perception of…

32 min
Fuck Dutch mass-surveillance: let's have a referendum!
Forcing the Netherlands to publicly debate privacy and the…
36 min
Understanding the Snooper’s Charter
Theresa May’s effort to abolish privacy
43 min
#xfilesgdpr
Datenschutz-Mythen aus 5 Jahren DS-GVO

57 min
Everything you want to know about x86 microcode, but might have been afraid to ask
An introduction into reverse-engineering x86 microcode and…
45 min
HbbTV Security
OMG - my Smart TV got pr0wn3d

30 min
The Magical Secrecy Tour
A Bus Trip into the Surveillance Culture of Berlin One Year…
33 min
Structuring open hardware projects
experiences from the “i3 Berlin” 3D printer project with…
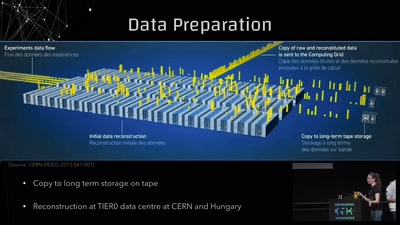
41 min
Conquering Large Numbers at the LHC
From 1 000 000 000 000 000 to 10: Breaking down 14 Orders…

58 min