Search for "Ben" returned 8967 results

52 min
Recent Developments in EU Data Retention proposals
Commission vs. Council - the lesser of two evils?

57 min
Hacking SCADA
how to own critical infrastructures

48 min
Breaking WEP in less than 60 Seconds
the next level

49 min
Does Hacktivism Matter?
How the Btx hack changed computer law-making in Germany
54 min
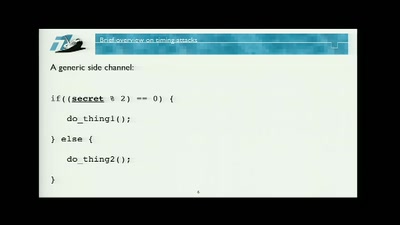
Time is NOT on your Side
Mitigating Timing Side Channels on the Web

61 min
Running your own GSM stack on a phone
Introducing Project OsmocomBB

50 min
Design Noir
The seedy underbelly of electronic engineering
56 min
SCADA Strangelove
or: How I Learned to Start Worrying and Love Nuclear Plants
68 min
The future of protocol reversing and simulation applied on ZeroAccess botnet
Mapping your enemy Botnet with Netzob

61 min
CSRF, the Intranet and You
Causes, Attacks and Countermeasures

44 min
GNU Radio & the Universal Software Radio Peripheral
Current Capabilities and Future Directions
41 min
Hacking on the Nanoscale
Dual Beam Devices for Rapid Prototyping and Reverse…

54 min
W3C on Mobile, CSS, Multimodal and more
A look at the upcoming standards by W3C

36 min
Who's snitching my milk?
Nonlinear dynamics/analysis of vanishing bovine products in…
![Advanced Buffer Overflow Methods [or] Smack the Stack](https://static.media.ccc.de/media/congress/2005/22C3-491-en-advanced_buffer_overflow_methods.jpg)
11 min
Advanced Buffer Overflow Methods [or] Smack the Stack
Cracking the VA-Patch
40 min
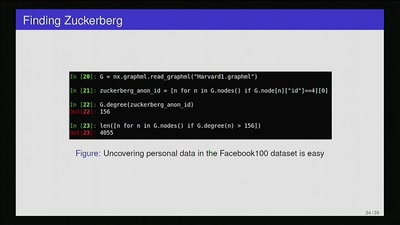
Privacy Invasion or Innovative Science?
Academia, social media data, and privacy

76 min
Messing Around with Garage Doors
Breaking Remote Keyless Entry Systems with Power Analysis

44 min
Port Scanning improved
New ideas for old practices

59 min
Deceiving Authorship Detection
Tools to Maintain Anonymity Through Writing Style & Current…

56 min