Search for "Leah" returned 1406 results

60 min
Intel Management Engine deep dive
Understanding the ME at the OS and hardware level

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

43 min
Forensic Architecture
Forensic Architecture is an independent research agency…

60 min
Lockpicking in the IoT
...or why adding BTLE to a device sometimes isn't smart at…
59 min
Top X* usability obstacles
*(will be specified later based on usability test with…

30 min
apertus° AXIOM
The first Open Source Cinema Camera

63 min
The Case Against WikiLeaks: a direct threat to our community
How to understand this historic challenge and what we can…

49 min
BREACH in Agda
Security notions, proofs and attacks using dependently…
72 min
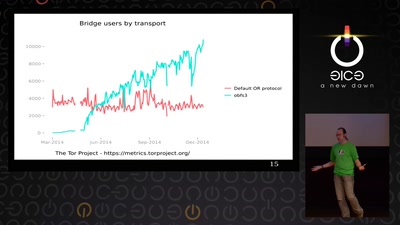
State of the Onion
Neuland
46 min
What The Fax?!
Hacking your network likes it's 1980 again

46 min
It's not safe on the streets... especially for your 3DS!
Exploring a new attack surface on the 3DS
56 min