Search for "Ben" returned 8971 results

50 min
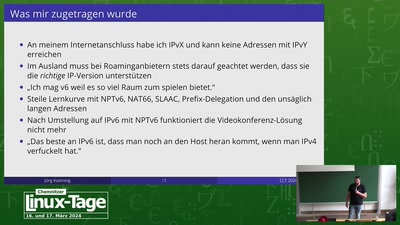
Console Hacking 2006
Xbox 360, Playstation 3, Wii
56 min
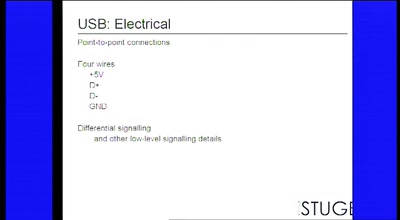
USB and libusb
So much more than a serial port with power
69 min
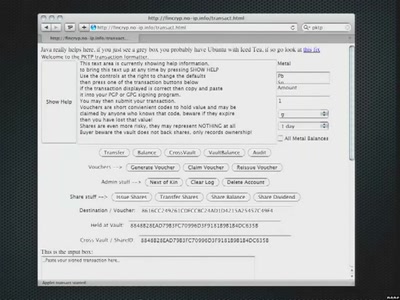
Financing The Revolution
Secure, private value transactions using digital cash

34 min
Lying To The Neighbours
Nasty effects with tracker-less BitTorrent
56 min
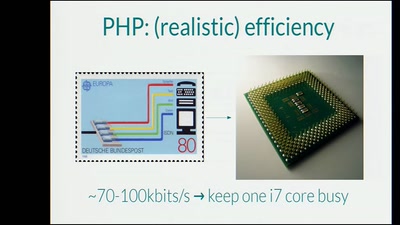
Effective Denial of Service attacks against web application platforms
We are the 99% (CPU usage)

63 min
Writing a Thumbdrive from Scratch
Prototyping Active Disk Antiforensics

61 min
MD5 considered harmful today
Creating a rogue CA Certificate

57 min
29C3 GSM: Cell phone network review
262 42 - The full spectrum

60 min
The worst part of censorship is XXXXX
Investigating large-scale Internet content filtering

55 min
Code, Sicherheit, Vertrauen
Wie openCode und das Badge Programm digitale Souveränität…

28 min
EVVA AirKey als Privacy-by-Design-Projekt
Zutrittskontrolle und Datenschutz - Ein vermeintlicher…

58 min