Search for "Sven" returned 2150 results
58 min
Firebird Open Source Database Quick Start
Why Firebird is a powerful alternative database system
55 min
YOU’VE JUST BEEN FUCKED BY PSYOPS
UFOS, MAGIC, MIND CONTROL, ELECTRONIC WARFARE, AI, AND THE…
40 min
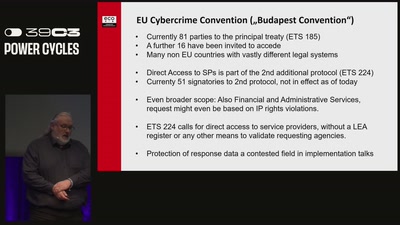
Live, Die, Repeat
The fight against data retention and boundless access to…
32 min
"Stimme in Konzerne hacken"
Herausforderungen & Lösungen um das Medium Podcast in…
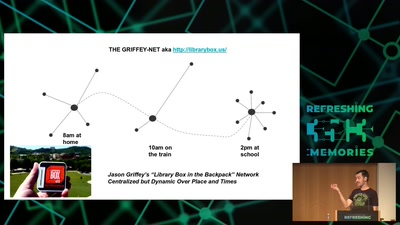
60 min