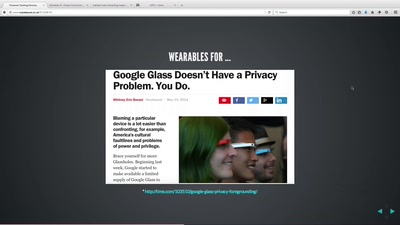
Search for "csk" returned 1261 results

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

45 min
Triggering Deep Vulnerabilities Using Symbolic Execution
Deep program analysis without the headache

55 min
Nach der Coronakrise ist mitten in der Klimakrise
Wege aus der Klimakrise - Was uns droht und was getan…

69 min
Grundrechte gelten nicht im Weltall!
Die absurdesten Szenen aus dem…

51 min
Uncovering vulnerabilities in Hoermann BiSecur
An AES encrypted radio system

45 min
To Protect And Infect
The militarization of the Internet

42 min
Firmware Fat Camp
Embedded Security Using Binary Autotomy
60 min
„Nach bestem Wissen und Gewissen“ – Floskeln in der Politik
Politische Phrasologie – warum man aus dem ganzen Zeug, das…
56 min
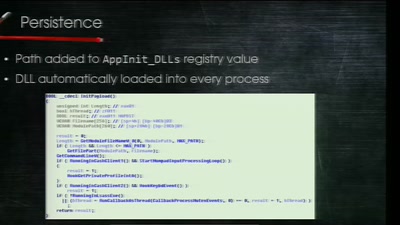
Electronic Bank Robberies
Stealing Money from ATMs with Malware

62 min
The Internet (Doesn't) Need Another Security Guide
Creating Internet Privacy and Security Resources That Don't…

58 min
Virtual Machine Introspection
From the Outside Looking In

63 min
The Cloud Conspiracy 2008-2014
how the EU was hypnotised that the NSA did not exist
60 min
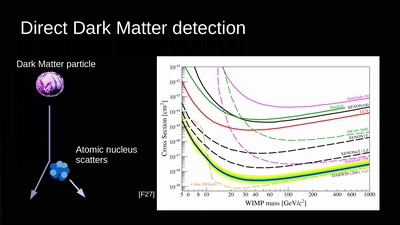
Let's reverse engineer the Universe
exploring the dark
60 min
Prediction and Control
Watching Algorithms

58 min
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
56 min