Search for "xif" returned 1978 results
61 min
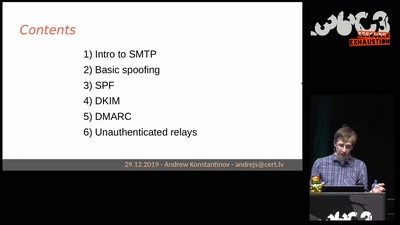
Email authentication for penetration testers
When SPF is not enough

38 min
Schnaps Hacking
from apple to schnaps -- a complete diy-toolchain

58 min
Switches Get Stitches
Industrial System Ownership

32 min
What's It Doing Now?
The Role of Automation Dependency in Aviation Accidents

51 min
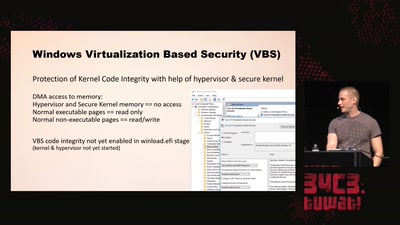
Virtual Secure Boot
Secure Boot support in qemu, kvm and ovmf.

60 min
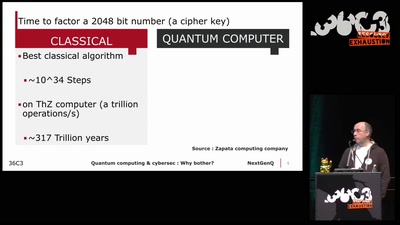
Quantum Cryptography
from key distribution to position-based cryptography

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety

53 min
Cryptography demystified
An introduction without maths
61 min
X Security
It's worse than it looks

60 min
The Exploration and Exploitation of an SD Memory Card
by xobs & bunnie

60 min
Crypto Wars Part II
The Empires Strike Back

67 min
The Maker movement meets patent law
How many windows are open in the patent fortress
46 min
Basics of Digital Wireless Communication
introduction to software radio principles

60 min
The plain simple reality of entropy
Or how I learned to stop worrying and love urandom

39 min
The automobile as massive data gathering source and the consequences for individual…
The next big privacy heist

60 min