Search for "Sven" returned 2150 results
53 min
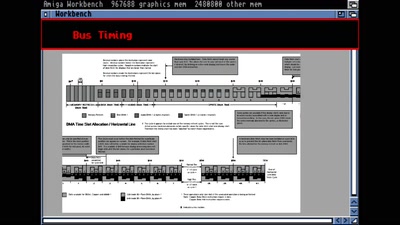
The Ultimate Amiga 500 Talk
Amiga Hardware Design And Programming

46 min
SELECT code_execution FROM * USING SQLite;
--Gaining code execution using a malicious SQLite database

50 min
The eXperimental Robot Project
An open-hardware bipedal walking machine

58 min
Baseband Exploitation in 2013
Hexagon challenges

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

55 min
What could possibly go wrong with <insert x86 instruction here>?
Side effects include side-channel attacks and bypassing…

39 min
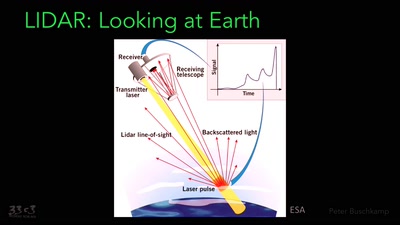
Greenhouse Gas Emission Data
Public, difficult to access, and not always correct

47 min
Bug class genocide
Applying science to eliminate 100% of buffer overflows

56 min
Viva la Vita Vida
Hacking the most secure handheld console

34 min
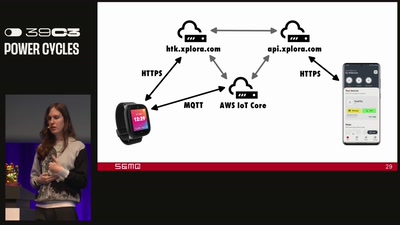
Little Services, Big Risks
Extending capability-based security models to achieve…
56 min
phyphox: Using smartphone sensors for physics experiments
An open source project for education, research and tinkering

63 min