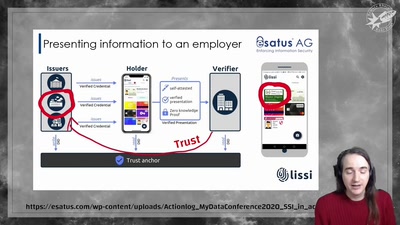
Search for "csk" returned 1264 results
60 min
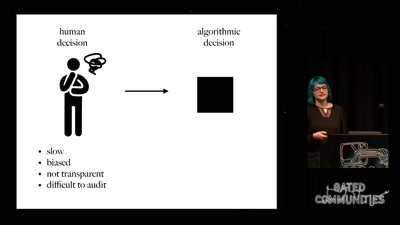
Prediction and Control
Watching Algorithms

58 min
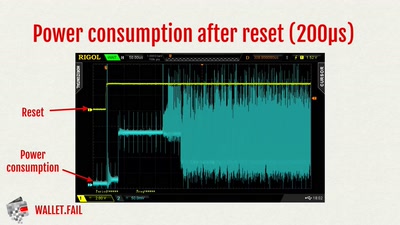
Self-encrypting deception
weaknesses in the encryption of solid state drives (SSDs)
61 min
wallet.fail
Hacking the most popular cryptocurrency hardware wallets
58 min
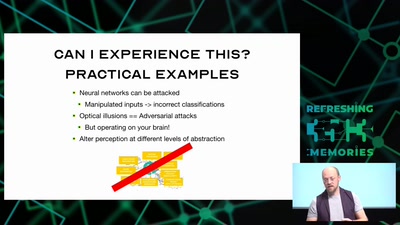
Hacking how we see
A way to fix lazy eye?

56 min
Viva la Vita Vida
Hacking the most secure handheld console

58 min
When hardware must „just work“
An inside look at x86 CPU design
91 min
What the World can learn from Hongkong
From Unanimity to Anonymity

74 min
Die EU im Krisenmodus
Was bedeutet das für die Zukunft
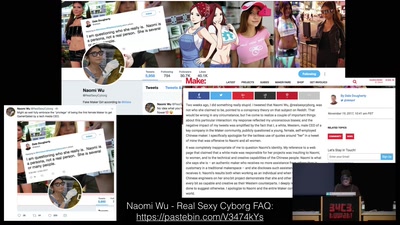
56 min
Deconstructing a Socialist Lawnmower
Obsolete Technologies + Critical Material Studies in Media…
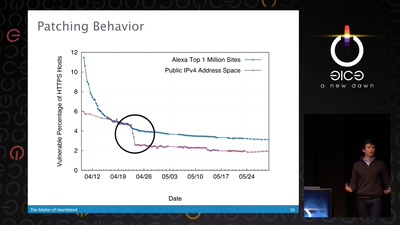
50 min
The Matter of Heartbleed
What went wrong, how the Internet reacted, what we can…

54 min