Search for "nerd" returned 2129 results

57 min
Protecting the Wild
Conservation Genomics between Taxonomy, Big Data,…

62 min
Kyber and Post-Quantum Crypto
How does it work?
41 min
Framing digital industry into planetary limits and transition policies
The environmental costs of digital industry and pathways to…

62 min
Space Ops 101
An introduction to Spacecraft Operations
52 min
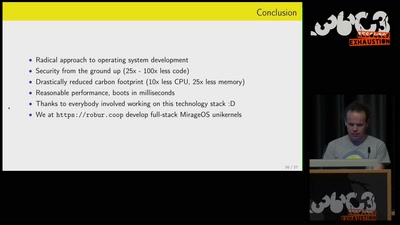
Leaving legacy behind
Reducing carbon footprint of network services with MirageOS…

59 min
How to teach programming to your loved ones
Enabling students over example-driven teaching
59 min
Scientific Literacy 101
Let's understand how the scientific system works

30 min
Shut Up and Take My Money!
The Red Pill of N26 Security

60 min
LibreSilicon
Decentralizing semiconductor manufacturing
53 min
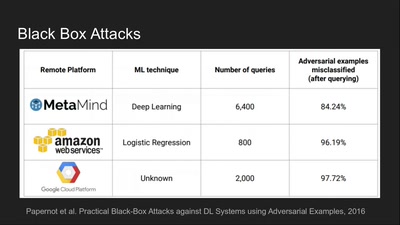
Deep Learning Blindspots
Tools for Fooling the "Black Box"
36 min