Search for "Apex" returned 174 results
66 min
31C3 Keynote
A New Dawn

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation
42 min
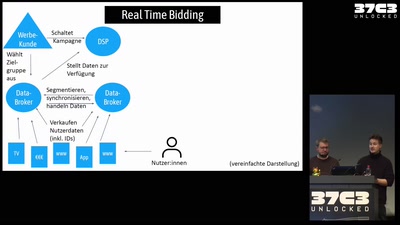
Die Akte Xandr
Ein tiefer Blick in den Abgrund der Datenindustrie

34 min
Scuttlebutt
The decentralized P2P gossip protocol

60 min
the possibility of an army
phone verified accounts bringing the Hessian army back to…

31 min
JODI - Apache is functioning normally
A net.art collective since 1995. Understanding the browser…

30 min
Rowhammer.js: Root privileges for web apps?
A tale of fault attacks on DRAM and attacks on CPU caches
55 min
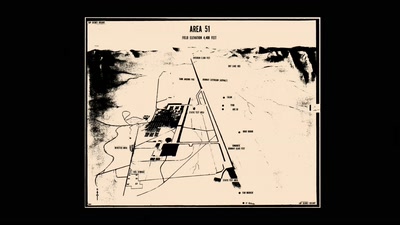
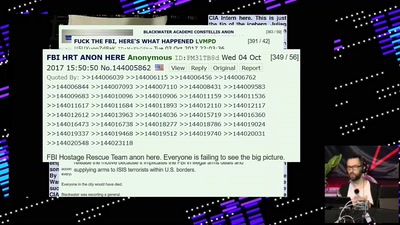
YOU’VE JUST BEEN FUCKED BY PSYOPS
UFOS, MAGIC, MIND CONTROL, ELECTRONIC WARFARE, AI, AND THE…
37 min
Butterbrotdosen-Smartphone
Mein DIY-Smartphone-Bau
41 min
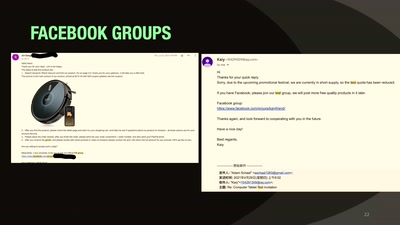
Our Time in a Product Review Cabal
And the malware and backdoors that came with it.

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

32 min
Craft, leisure, and end-user innovation
How hacking is conceived in social science research

57 min
“I feel like a criminal and I have to be god at the same time”
Perceptions of hackers and hacktivists on their…
63 min