Search for "Benks" returned 123 results

64 min
Decoding the LoRa PHY
Dissecting a Modern Wireless Network for the Internet of…

49 min
Key-logger, Video, Mouse
How to turn your KVM into a raging key-logging monster
60 min
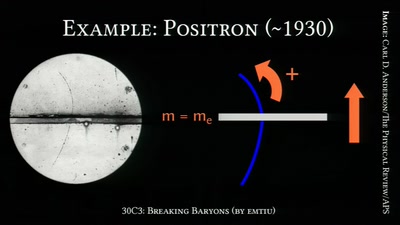
Breaking Baryons
On the Awesomeness of Particle Accelerators and Colliders
61 min
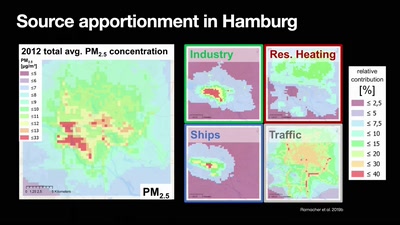
Numerical Air Quality Modeling Systems
a journey from emissions to exposure

61 min
Ten years after ‚We Lost The War‘
The future does not look much brighter than ten years ago.…
60 min
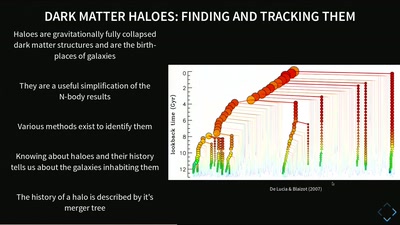
Simulating Universes
What Virtual Universes Can Tell Us About Our Own

61 min
Code Pointer Integrity
... or how we battle the daemons of memory safety
65 min
35C3 Infrastructure Review
Up and to the right: All the statistics about this event…
44 min
Replication Prohibited
3D printed key attacks

58 min
How to Break PDFs
Breaking PDF Encryption and PDF Signatures

61 min
Now I sprinkle thee with crypto dust
Internet reengineering session

55 min
Graphs, Drones & Phones
The role of social-graphs for Drones in the War on Terror.

51 min
Ecuador: how an authoritarian government is fooling the entire world
Guess what? The Government of Rafael Correa actually is…

69 min
cryptocurrencies, smart contracts, etc.: revolutionary tech?
short answer: Yes!

60 min