Search for "Marek" returned 382 results

41 min
Frontex: Der europäische Grenzgeheimdienst
Das Grenzüberwachungssystem EUROSUR führt Aufklärungsdaten…
83 min
Der Weisheit
Eine Stunde Lebenskunde - 10. Staffelfinale

36 min
Apple's iPhone 15: Under the C
Hardware hacking tooling for the new iPhone generation

29 min
2 Takte später
30C3S SCE mbH: GEMA-Konkurrenz für Fortgeschrittene

48 min
Don't Ruck Us Too Hard - Owning Ruckus AP Devices
3 different RCE vulnerabilities on Ruckus Wireless access…
60 min
Inside the Fake Like Factories
How thousands of Facebook, You Tube and Instagram pages…
38 min
CPU Entwicklung in Factorio
Vom D-Flip-Flop bis zum eigenen Betriebssystem

42 min
NEW IMPORTANT INSTRUCTIONS
Real-world exploits and mitigations in Large Language Model…

60 min
Beyond your cable modem
How not to do DOCSIS networks
42 min
Netzpolitischer Wetterbericht 2018
Die Höhen und Tiefen der deutschen und europäischen…

44 min
Disclosure DOs, Disclosure DON'Ts
Pragmatic Advice for Security Researchers

39 min
Recharge your batteries with us
– an empowering journey through the energy transition
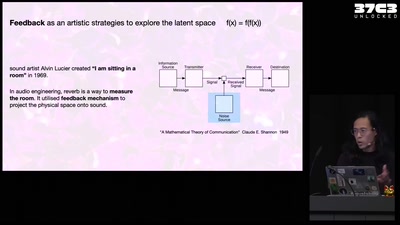
53 min
Self-cannibalizing AI
Artistic Strategies to expose generative text-to-image…

17 min