Search for "Matt Hardy" returned 244 results
44 min
Replication Prohibited
3D printed key attacks

21 min
Nerds touching grass
Let’s start a bio-hackspace-revolution
40 min
Never Forgetti
a didactic live-gaming performance about dying women across…
60 min
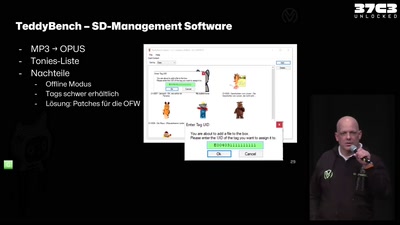
Toniebox Reverse Engineering
Eine Musikbox für Kinder, Maker und Hacker

60 min
APT Reports and OPSEC Evolution, or: These are not the APT reports you are looking for
How advanced threat actors learn and change with innovation…

32 min
Visceral Systems
Approaches to working with sound and network data…

62 min
To Protect And Infect, Part 2
The militarization of the Internet
59 min
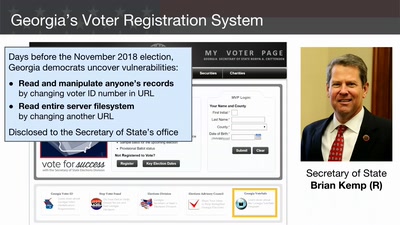
Election Cybersecurity Progress Report
Will the U.S. be ready for 2020?

42 min
Reverse engineering FPGAs
Dissecting FPGAs from bottom up, extracting schematics and…
39 min
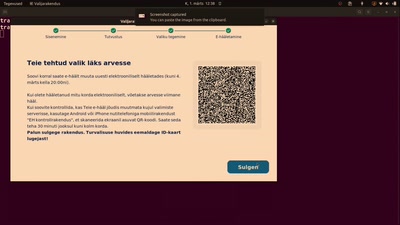
Should e-voting experience of Estonia be copied?
Observer report of 2023 parliamentary elections
66 min
31C3 Keynote
A New Dawn

60 min
From Computation to Consciousness
How computation helps to explain mind, universe and…

58 min
The Magic World of Searchable Symmetric Encryption
A brief introduction to search over encrypted data
58 min
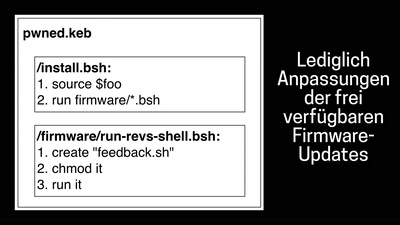
Operation Triangulation
What You Get When Attack iPhones of Researchers
52 min