Search for "Various Speakers" returned 193 results
58 min
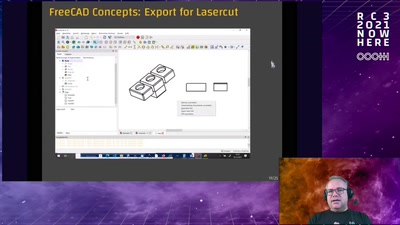
Script Your Car!
Using existing hardware platforms to integrate python into…

41 min
Locked up science
Tearing down paywalls in scholarly communication

58 min
Thwarting Evil Maid Attacks
Physically Unclonable Functions for Hardware Tamper…
47 min
Going Deep Underground to Watch the Stars
Neutrino Astronomy with Hyper-Kamiokande

60 min
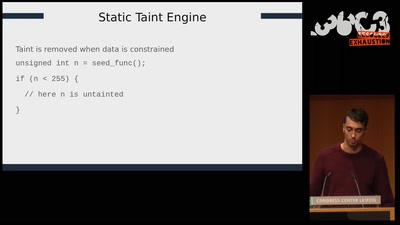
Lets break modern binary code obfuscation
A semantics based approach
33 min
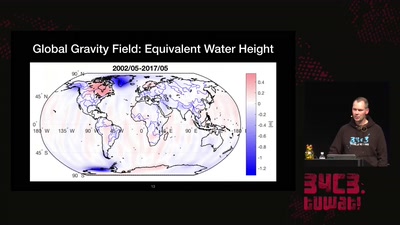
Watching the changing Earth
warning: gravity ahead

59 min
Fernvale: An Open Hardware and Software Platform, Based on the (nominally) Closed-Source…
A Lawful Method for Converting Closed IP into Open IP
60 min
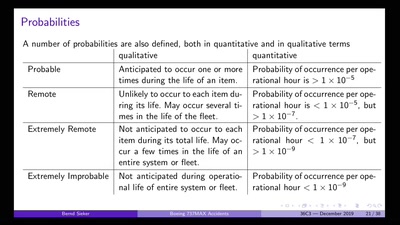
Boeing 737MAX: Automated Crashes
Underestimating the dangers of designing a protection system
32 min
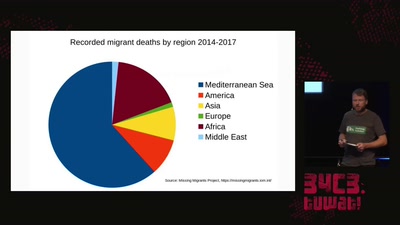
The seizure of the Iuventa
How search and rescue in the mediterranean was criminalized
22 min
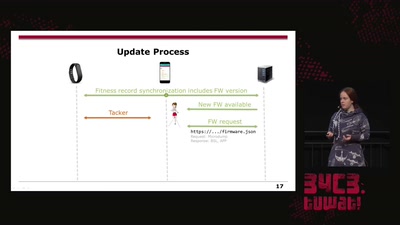
Doping your Fitbit
On Fitbit Firmware Modifications and Data Extraction
31 min
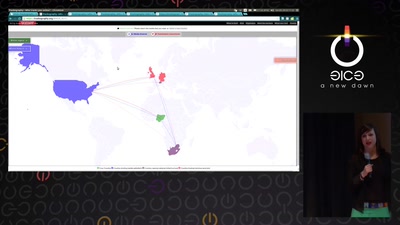
Trackography
You never read alone

64 min
It Always Feels Like the Five Eyes Are Watching You
Five Eyes’ Quest For Security Has Given Us Widespread…
37 min
Listening Back Browser Add-On Tranlates Cookies Into Sound
The Sound of Surveillance
32 min
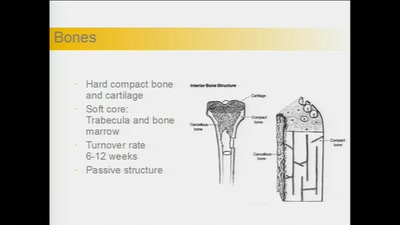
Coding your body
How to decipher the messages of your body
44 min
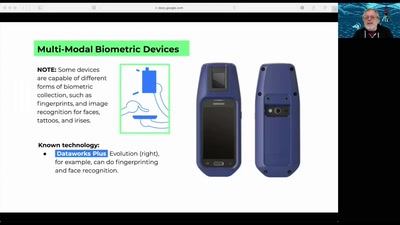
Spot the Surveillance
How to Identify Police Surveillance at Protests and Large…

35 min
Harry Potter and the Not-So-Smart Proxy War
Taking a look at a covert CIA virtual fencing solution
38 min
ARMore: Pushing Love Back Into Binaries
Aarch64 binary rewriting adventures but mostly pains

50 min
How does the Internet work?
An explanation of Inter-Net and everyday protocols

29 min